Cybersecurity
The cause of 95% of all security breaches, can be found in phishing attacks.
Act now, before the attackers do.
Protection against cyber attacks must be part of the focus of any business. Maximizing security ensures the continuity of your business. Protection starts with the email. Use email certificates to encrypt your messages.
To best protect your IT infrastructure, you should be able to answer the following questions:
- Is your data protected against attacks?
- Is your backup working?
- Does data recovery work in an emergency?
- Can I become a victim of a cyber attack?
- Does an emergency plan exist?
- Are the programs up to date?
If you cannot agree with all of these questions, then it is high time to act.
Should you wish to take out cyber insurance, it is mandatory to answer yes to these questions. To prepare a cyber insurance policy, we work with a checklist, point by point, so that you achieve the specifications.
The know-how of your company guarantees the continuity of your business and the economy, worldwide.
Neutral consulting
We make our security advice available to insurance companies and businesses. The neutral audits provide companies with an overview of their current system security. The state contains recommendations and possible measures to adjust the security. This helps companies to minimise risks and insurance companies to offer their cyber insurance tailored to the company.
RISK-management
We help our customers to have a secure IT environment. Based on the findings of the audits, we draw up catalogs of measures and prepare risk concepts tailored to the company. If there are changes in the risk development, we provide advice, inform the customer about possible security proposals and adjustments.
Consulting – Our competencies
Our services are offered as a service for security-related issues. Weak points in IT infrastructures must be identified and corrected. We create a security concept for you with a risk analysis in the areas of information management – processes and infrastructures.
This work is always carried out in dialogue with you and our specialists. Activities can be implemented in a targeted and timely manner. Since you are involved in the process flow, you have a broader basis for your decision support.
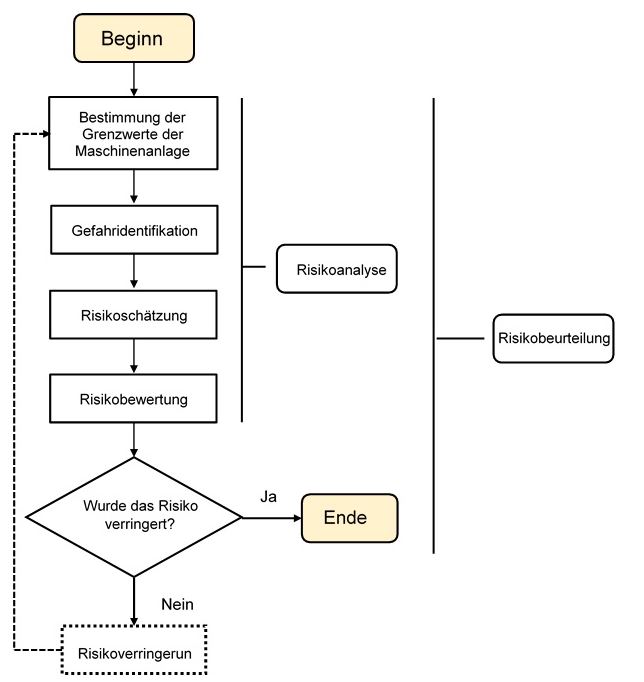
Competencies
We create security concepts for you with risk analyzes in areas such as:
- Threat analysis (Dangers from the Internet)
- Use of known operational procedures and protective measures
- Cybersecurity with the involvement of ethical hackers
- STEP-analysis
- RISK-identification
- RISK-analysis
- RISK-evaluation
- RISK-management
Information management:
- Professional advice and support
– strategically
– operational
– safety-related
– Authorities IT
– IT safety - Execution of assemblies and analyzes
- Creation of specification sheets for systems, training and operation
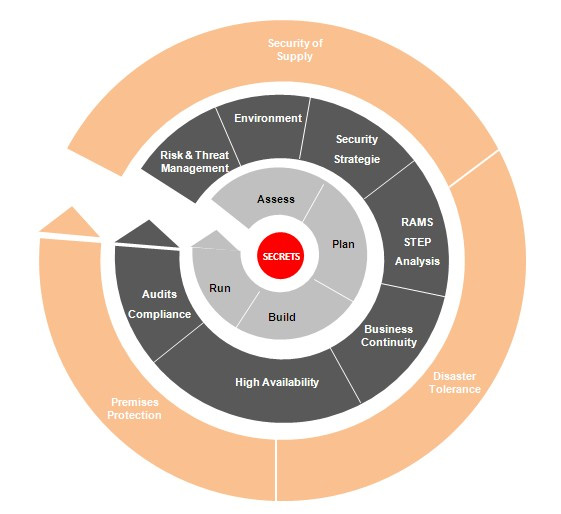
How we work
mySwissKeyPartners has set itself the goal of fulfilling all customer requests as required and ensuring this by means of the SSCG management strategy.
These are considered over the entire life cycle:
- Project planning, project management and project responsibility in all project phases
- Responsibility for the legal, regulatory and organizational processes
- Organization or monitoring of all logistical processes, infrastructures, personnel
- Supervision of planning, installation and commissioning for the customer
- Selection, training, security control, know-how transfer according to the training concept
- Assessments and Audits
